ATS Single Sign On Solutions
Integrating third party platforms with iMIS
We believe that members should have a consistent login experience across all platforms. That means that the experience to login, create account, forgot password, forgot username, and logout are the same each time the member interacts with your organization.
ATS has the tools!
In working with dozens of vendors, we find that not all vendors interact with an SSO the same way. To accomplish this, ATS has developed a number of solutions and techniques to help you solve the SSO challenge. If you have a Content Management System, Learning Management System, or even a homegrown application, ATS has the SSO solution for you. Our toolbox includes SAML, OAuth, Open ID, token-based, and cookie-based solutions. Our solutions with traditional on-premise iMIS clients and even iMIS Cloud clients. Our simple SSO solutions, and many of our bridge installations, also support a single logout.
How do I get started?
The first step is to see if ATS has already built an integration with your third party vendor. ATS has worked with dozens of vendors to co-develop and deploy Single Sign On solutions. These are pre-built, off-the-shelf, ready-to-install products for third party integration with iMIS. Review the list of our existing bridges and integrations here: ATS Bridges & Integrations
Common Solutions
These solutions are not vendor specific and can be licensed from ATS. ATS will install these products on your server and work with your third party vendor to provide support during the installation and testing process.
- Standards based SSO – Using providers like Okta, you can use iMIS as an identity provider for Okta and then use Okta as an identity provider for other applications that act as a Service Provider. This will leverage iMIS credentials while providing the flexibility of a well known provider, Okta.
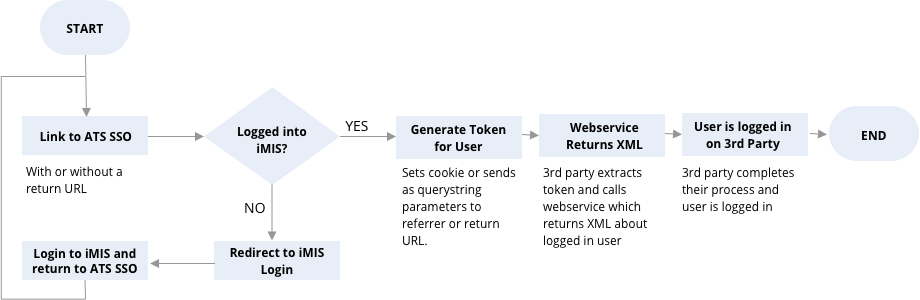
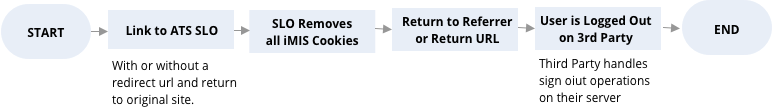
- Token-based SSO - A token based solution is one of the most straightforward implementation. It can be used by most and is especially useful for custom built applications and integrations with custom developers. The ATS solution provides a single sign on and a single logout solution. The basic premise is that there is a transparent pass through page (think of this as a gatekeeper). This pass through page will check to see if the person is logged in or not. If they are not it will send them to the iMIS login page. If they are logged in, it will send them to the third party website. When it sends the person to the third party website it will append a token to the url. That token can then be used by the third party to call a webservice to return any data from that person based on an IQA. That means that you can send anything back that can be put in an IQA including , contact information, membership status, and even committee participation. A single logout function will allow the third party to logout of iMIS at the same time as they logout of their third party application.
- Cookie-based SSO - A cookie based solution is one of the most straightforward implementation. This is best used when the two systems can share the same domain or subdomain, since cookies cannot be read by other domains. The ATS solution provides a single sign on and a single logout solution. The basic premise is that there is a transparent pass through page (think of this as a gatekeeper). This pass through page will check to see if the person is logged in or not. If they are not it will send them to the iMIS login page. If they are logged in, it will create a cookie with a token and then it will send them to the third party website. That cookie can then be read by the third party. The token in the cookie can be used by the third party to call a webservice to return any data from that person based on an IQA. That means that you can send anything back that can be put in an IQA including , contact information, membership status, and even committee participation. A single logout function will allow the third party to logout of iMIS at the same time as they logout of their third party application.
These examples demonstrate the flow for a Single Sign On, a Single Log Off, and the methodology to determine if someone is logged into iMIS without passing them through the Single Sign On using JSONP.
ATS Token or Cookie-base Single Sign On
ATS Token or Cookie-base Single Log Off
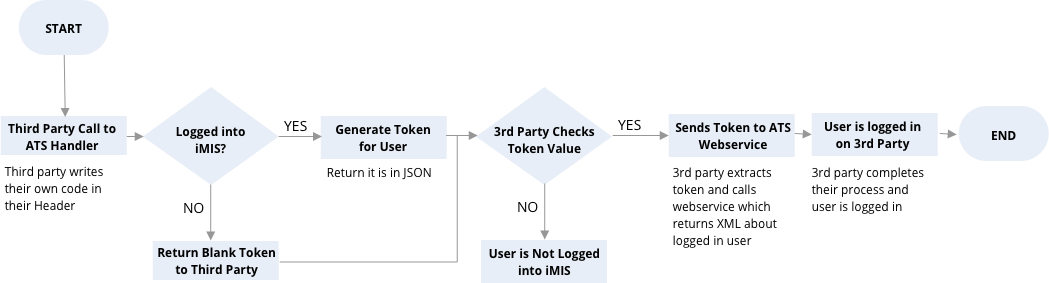
JSONP stands for "JSON with Padding" (and JSON stands for JavaScript Object Notation). This is a way to get data from another domain that bypasses CORS (Cross Origin Resource Sharing) rules. This is useful for a third party system to "ping" iMIS to determine if the person is logged in. If the person is logged in, then the JSONP will return a token which can be used to get information from the webservice without passing the person through a login page. This can be used for determining if the third party should show a signin or signout page on their home page and for showing "Welcome Randy" on the third party site without pushing the person through a login.
ATS JSONP Method to Determine if Someone is Logged in to iMIS
- SAML - SAML stands for Security Assertion Markup Language. It is a common protocol for web browser single sign on using secure tokens. It uses standard cryptography and digital signatures to pass a secure sign-in token from an identity provider to an application. ATS has deployed this solution for on-premise and iMIS Cloud clients. Since these integrations generally require tight coordination with the vendor, we ask that you contact ATS for additional information. Wikipedia Page on SAML
- OAuth - OAuth stands for Open Authorization. It is an open standard for token-based authentication and authorization. It allows an end user's account information to be used by third-party services without exposing the user's password. Since these integrations generally require tight coordination with the vendor, we ask that you contact ATS for additional information. Wikipedia Page on OAuth
- OpenID - OpenID is an open standard and decentralized authentication protocol. It allows uses to be authenticated by co-operating sites using a third party service. Since these integrations generally require tight coordination with the vendor, we ask that you contact ATS for additional information. Wikipedia Page on OpenID
Contact Us
Contact us with comments, questions or to request a quote.